Spring Security - Behind the Curtain
A comprehensive guide to decode the Architecture
This article focuses on an in-depth architectural overview of Spring Security. I can confidently say that this is one of the best breakdowns you have ever encountered on Spring Security, but there are some prerequisites that you should have before moving forward. They are:
Pre-requisites:
1. Understanding of Servlets
2. What is a Request and Response
3. Understanding of MVC Architecture
4. What is a Front Controller
Assuming you've got the foundational blocks in place, we're about to unwrap the intricate architecture of Spring Security.
The Breakdown 💥
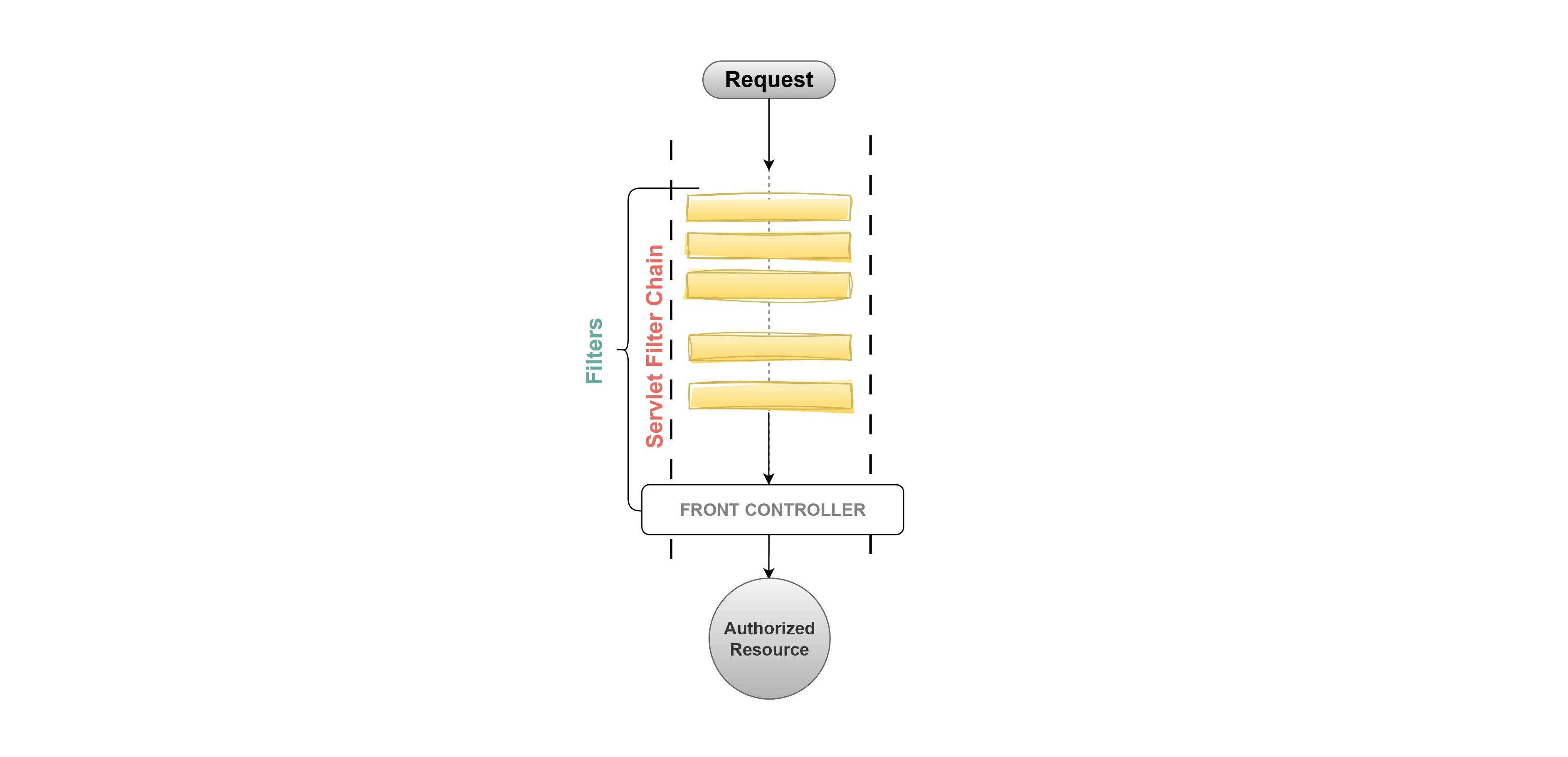
1. Servlet Filter Chain
The FilterChain is a component of the servlet container that plays a fundamental role in the Standard Servlet Request Processing Pipeline. The FilterChain contains a list of Filter objects in a proper sequential order.
Each filter in the filter chain performs a validation or customization logic on the incoming requests. This helps in assuring the authenticity of the incoming requests. e.g.,
Validation Filters: Verifying request content type, method type, authentication, authorization, parameters, etc.
Logging filters: for tracking request details.
Encryption filters: for secure data transmission.
Authentication filters: for user login and access control (usually added on the server side).
Any request that is coming from the client passes through the FilterChain of the Servlet Container, once the request passes through all the Filters, it proceeds to the Front Controller. The Front Controller then takes charge of routing the request to the appropriate resource for further handling and response generation.
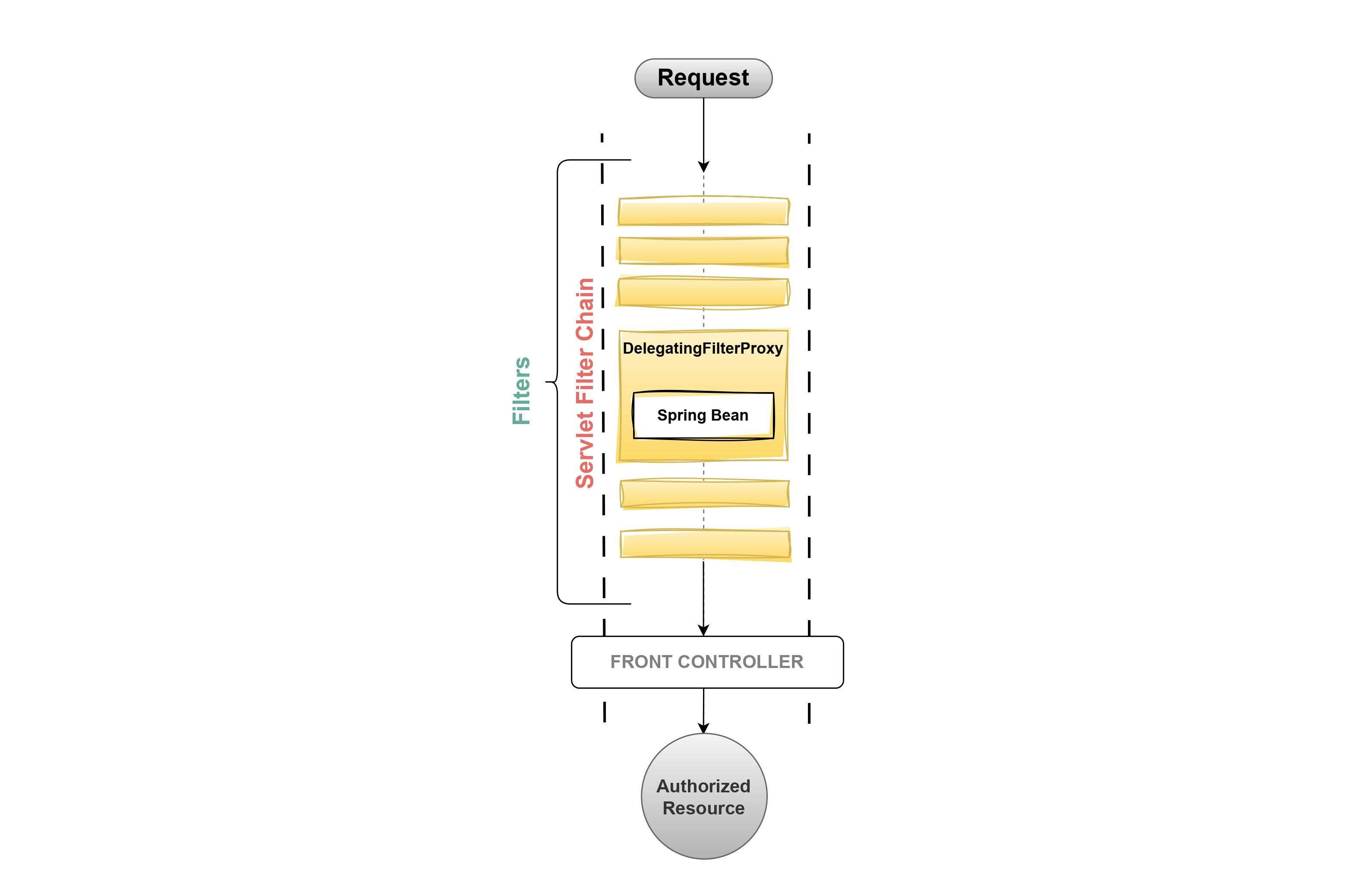
2. DelegationFilterProxy
DelegationFilterProxy is the Spring-Managed custom filter, it implements the Filter interface of
javax-servlet-api.DelegatingFilterProxy helps in delegating the request filtering process to another bean responsible for managing the Spring Security filters.
This step is very crucial in a Spring Security-driven application since the servlet container doesn't understand Spring Beans and their configuration.
3. Filter Chain Proxy
The
FilterChainProxyis responsible for managing a list ofSecurityFilterChainbeans.When a request enters DelegatingFilterProxy it further delegates the filtering process to the
FilterChainProxy.The FilterChainProxy iterates over the list of SecurityFilterChain beans and tries to find a match (based on the URL pattern) for the current request.
If a match is found, then the FilterChainProxy delegates the request to the SecurityFilterChain.
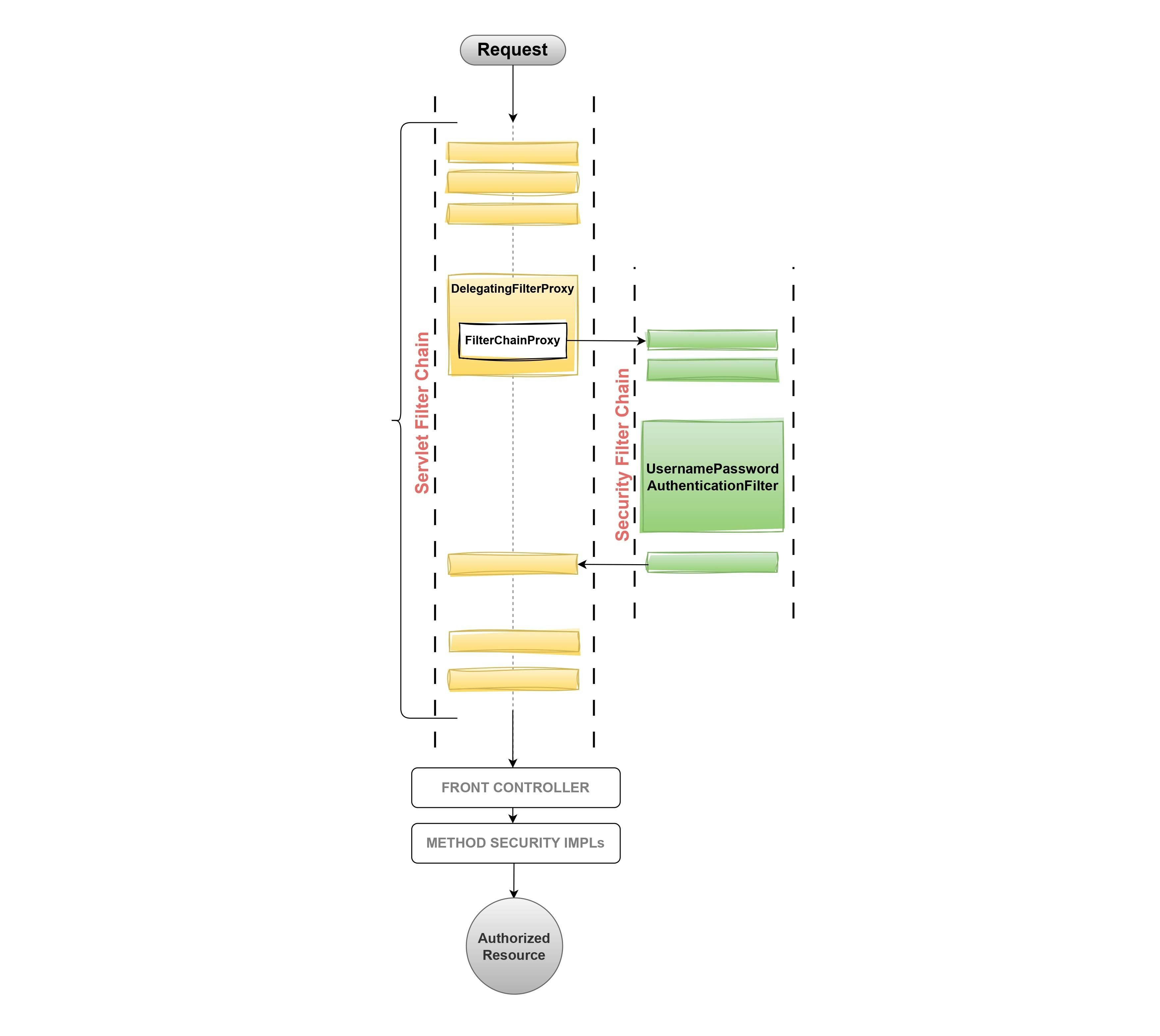
4. Security Filter Chain
The SecurityFilterChain contains a list of Filter objects that are specific to the security requirements of the request.
Each SecurityFilterChain iterates through its list of filters, sequentially executing them.
If any filter in the SecurityFilterChain returns a negative response, the request is denied.
If all filters in the SecurityFilterChain pass successfully, the request proceeds to the next filter or servlet responsible for handling it.
5. UsernamePasswordAuthenticationFilter
UsernamePasswordAuthenticationFilteris one of the filters ofSecurityFilterChain, which by default does In-Memory authentication to a default usernameuserand a randomly generated password that gets printed in the console. This is done to set up the project quickly but it is not recommended to be used.This In-Memory authentication behaviour is what we have seen in the previous article Spring Security - The Magic First Approach of this series. Where Spring Security by default had a user named
userand generated the password during the application startup.
Authentication Architecture
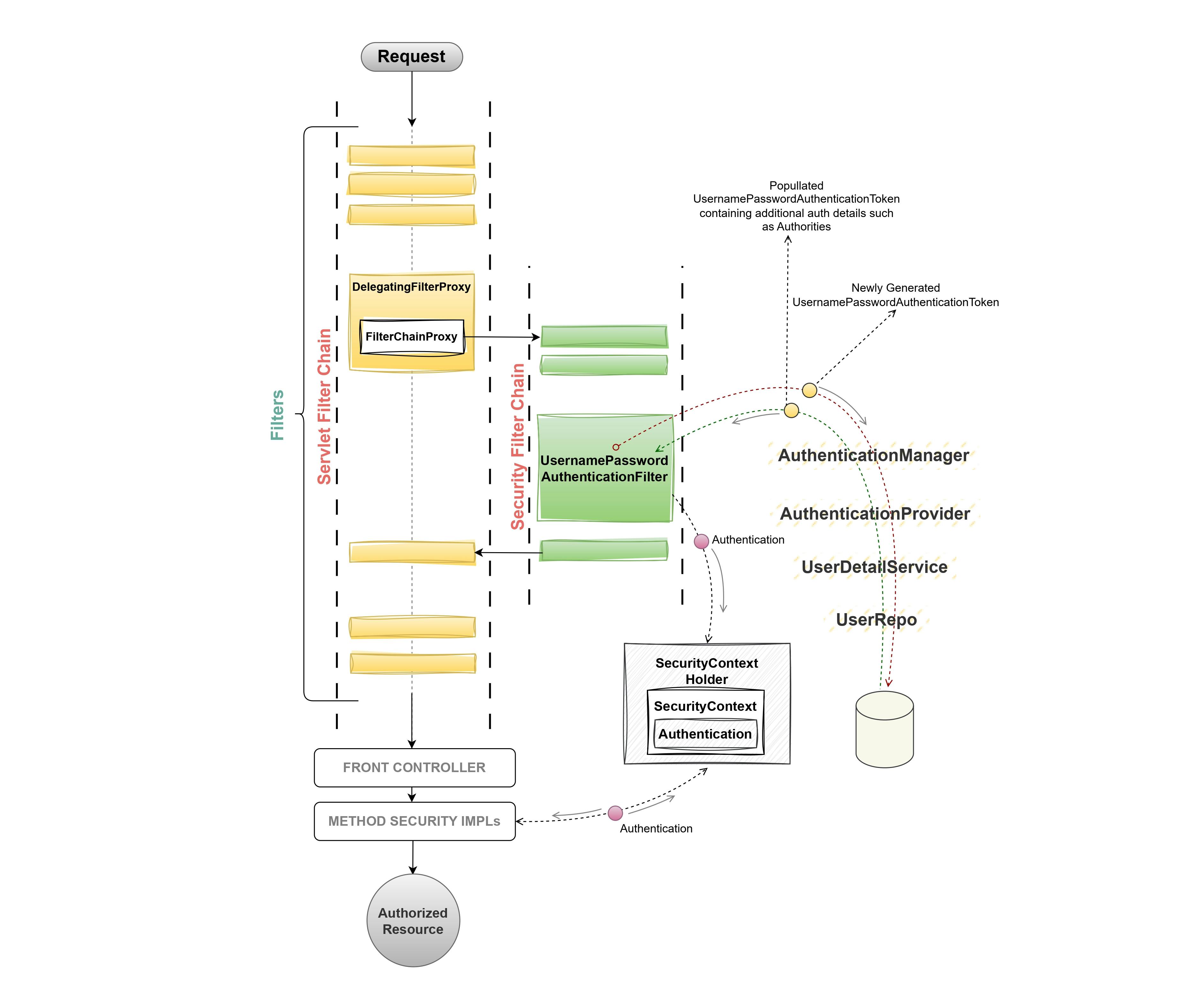
The request from the client passes through the Servlet
FilterChainand theDelegatingFilterProxydelegates the request to the SecurityFilterChain.The
SecurityFilterChaindelegates the request object to theUsernamePasswordAuthenticationFilter, which generates a UsernamePasswordAuthenticationToken using user credentials.The
UsernamePasswordAuthenticationTokenis later passed to theAutheticationManager, It contains a list of AutheticationProviders each containing its Authentication logic.The
AutheticationProvideris generally an interface implemented byDaoAutheticationproviderto validate the user credentials against the database.If the user is successfully authenticated, the
UsernamePasswordAuthenticationTokenis further populated andThe authentication object is set to
SecurityContextofSecurityContextHolder.The
SecurityContextholds the authentication object throughout the request processing time. One SecurityContextHolder can hold only one SecurityContext at a time.
Conclusion:
In conclusion, this article provides a comprehensive analysis of Spring Security's architecture, offering valuable insights into its core functionalities. By delving into the key components of Spring Security such as the Servlet Filter Chain, DelegationFilterProxy, Filter Chain Proxy, Security Filter Chain, and UsernamePasswordAuthenticationFilter, the article facilitates a thorough understanding of Spring Security's authentication management. With its clear explanations and illustrative diagrams, this article serves as a valuable resource for developers seeking to implement robust security measures within their Spring applications.
The subsequent article in this series will explore the practical implementation of Spring Security for database-based authentication. Feel free to leave a comment for any queries or to engage in discussion related to this topic.
