Spring Security: Overview of Authentication and Authorization Workflows
Master the basics of authentication and authorization workflows in this simplified guide.

Table of contents
The major aspects of security in an application are authentication and authorization, Authentication is a process of validating the user for what he claims to be and Authorization is the process of defining what exact resources of an application should be accessed by the particular user.
Authentication
Now let's understand how exactly the authentication process works. For example, consider an e-commerce application that has the following endpoints.
"/register"- used to register or create an account.
Whenever a user tries to register himself to an e-commerce type of application, he usually requests to register as a seller or a customer. The application processes the request and validates the user input. If the user data is valid, a proper success message along with a login page as a response is returned.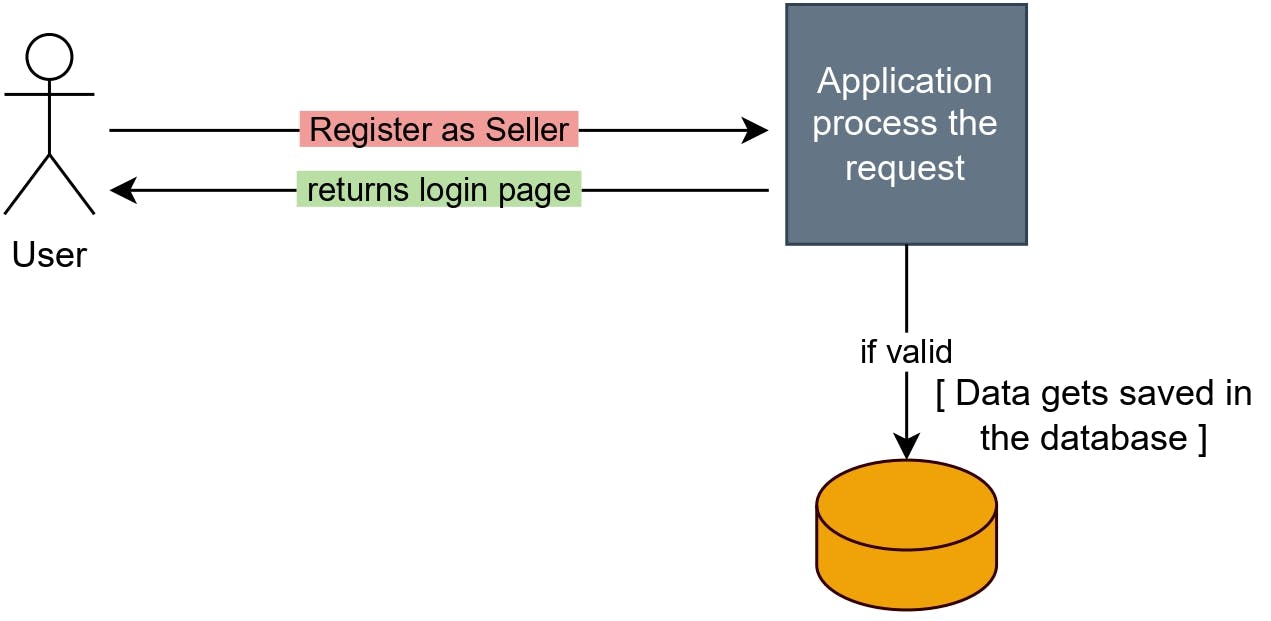
"/login"- used to authenticate the user.
After the successful registration, the user next tries to log in. The login process is important because it is where the application starts to track the user. There are several ways to implement a user-tracking system in an application, some of them are Hidden-Form-Fields, Cookies, HttpSession, Tokens, etc., and Each of them is used in different ways and for different purposes.HttpSession is one of the most common ways to achieve authentication and authorization in the application. The feature of HttpSession is that it stores the user details on the server side and manages a session for the user between login and logout.
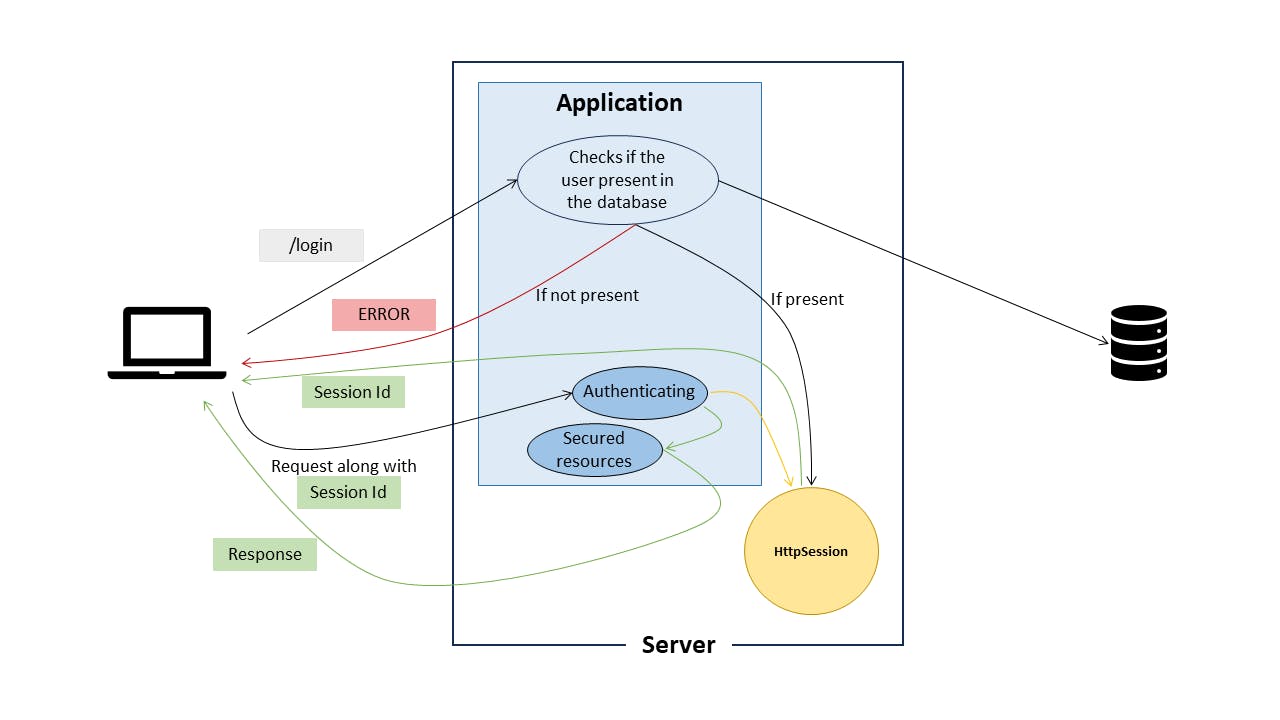
Spring Security internally maintains an HttpSession for every user authenticated. Whenever there is a request to "/login" endpoint, (the request must contain username and password as the body). The application validates the username and password against the database, if the user is found with the given credentials, an HttpSession is created. The HttpSession is created on the server side and will contain the user details. Later a sessionId is sent to the client as a cookie.
When the user wants to access any resource of the application, he has to send the sessionId along with the request (this is internally done by the browser itself, so the developer need not have to worry about sending a sessionId through every request). If the sessionId gets validated with the session present in the server, the user will be able to access the resources securely.
summary
Once the user is successfully registered to the application, he will be able to login and access the application resources securely. When the user sends a login request -> the application processes the request and validates the username and password against the database. -> If the user is successfully authenticated an HttpSession is created in the database -> Later a sessionId is sent to the user. -> This sessionId can later be used by the user to authenticate himself to access the application resources.
Authorization
Authorization is used to perform access control within the application. This is important because in an application there can be multiple roles each having their own responsibilities. Let's consider an e-commerce application where users can have roles such as seller & customer. There can be several endpoints like this as follows:
"/inventories/{inventoryId}/products"- used to add the product to a particular inventory, only the seller should be able to add the product."/carts/{cardId}/products/{productId}"- used to add the product to a particular cart, only the customer should able to perform this operation."/products"- used to fetch all the products from the database, both Seller & Customer should be able to perform this operation"/products/{productId}"- used to fetch a particular product based on the productId, both seller & customer should be able to perform this operation.
As you can see above there are different aspects of an application that should be reserved for a user with a specific role. A customer should never be able to create inventories and add products, Seller should never deal with the cart. So this type of access control is important to improve the application's data integrity as well as the user experience.
Conclusion
Authentication is a process of ensuring the user is valid and unique and Authorization is the process of defining what exact resource the user should be able to access and what should not be accessed.
This article focussed more on the broader overview of authentication and authorization workflows. In the upcoming article of this series Walk-Through Spring Security, we will dive deep into the architectural level of authentication and authorization process. I hope you found this article useful, feel free to leave a comment if there are any queries.
